Modular Policy Framework (MPF) configuration defines set of rules for applying firewall features, such as traffic inspection, QoS etc. to the traffic transiting the firewall
There are 3 main components in creating a MPF.
1) Class Map
Class map is used to identify the type of traffic. This can be done by creating an ACL.
2) Policy Map
Policy Map specifies what action the ASA should take against the traffic identified by the Class Map.
3) Service Policy
Finally Service policy specifies where to apply it. The policy is applied to an interface or Globally.
Udacity has special offers worldwide to help anyone learn important, higher-paying job skills during this challenging time. Click here to get your offer and start learning now!
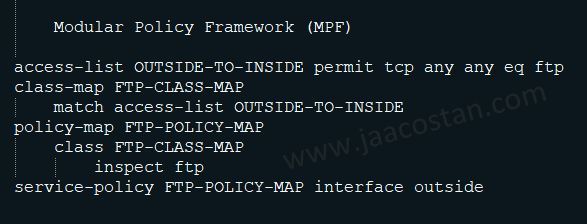
access-list OUTSIDE-TO-INSIDE permit tcp any any eq ftp
<--- The above ACL will allow FTP traffic. This ACL can be different than the Interface ACL--->
class-map FTP-CLASS-MAP
match access-list OUTSIDE-TO-INSIDE
<--- The class map FTP-CLASS-MAP will look for the FTP traffic based on ACL --->
policy-map FTP-POLICY-MAP
class FTP-CLASS-MAP
inspect ftp
<--- What action need to be done? here inspect the ftp. --->
service-policy FTP-POLICY-MAP interface outside
<--- Apply the policy in the outside interface --->
The above illustration is just an example. MPF enables the administrator to assign different network policies to different traffic flows in a flexible and granular manner.
There are 3 main components in creating a MPF.
1) Class Map
Class map is used to identify the type of traffic. This can be done by creating an ACL.
2) Policy Map
Policy Map specifies what action the ASA should take against the traffic identified by the Class Map.
3) Service Policy
Finally Service policy specifies where to apply it. The policy is applied to an interface or Globally.
Udacity has special offers worldwide to help anyone learn important, higher-paying job skills during this challenging time. Click here to get your offer and start learning now! 
Sample Illustration
Consider the following Command lines.access-list OUTSIDE-TO-INSIDE permit tcp any any eq ftp
<--- The above ACL will allow FTP traffic. This ACL can be different than the Interface ACL--->
class-map FTP-CLASS-MAP
match access-list OUTSIDE-TO-INSIDE
<--- The class map FTP-CLASS-MAP will look for the FTP traffic based on ACL --->
policy-map FTP-POLICY-MAP
class FTP-CLASS-MAP
inspect ftp
<--- What action need to be done? here inspect the ftp. --->
service-policy FTP-POLICY-MAP interface outside
<--- Apply the policy in the outside interface --->
The above illustration is just an example. MPF enables the administrator to assign different network policies to different traffic flows in a flexible and granular manner.