JSON Web Token (JWT) is a standard for securely transmitting information between parties as a JSON object. This information can be verified and trusted because as it is digitally signed using the public/private keys. In this post, i will be explaining about the JWT and how it can be manipulated to perform certain functions, especially during penetration testing.
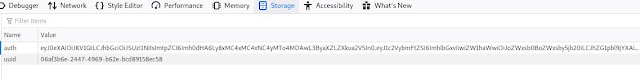
Access the website that uses JWT token and open the developer tools in the web-browser to see the JWT token. To decode the token, we can use a handy website https://jwt.io .Copy the token and paste it on the website to decode.You can see the key pair values.
And if you want to generate your own customized JWT token, you can do it in the same way. Create the header and the payload data based on your desired fields. The jwt.io site generates and sign the key using the key-pairs. Then copy the encoded token and re-transmit to the target website to do manipulation.